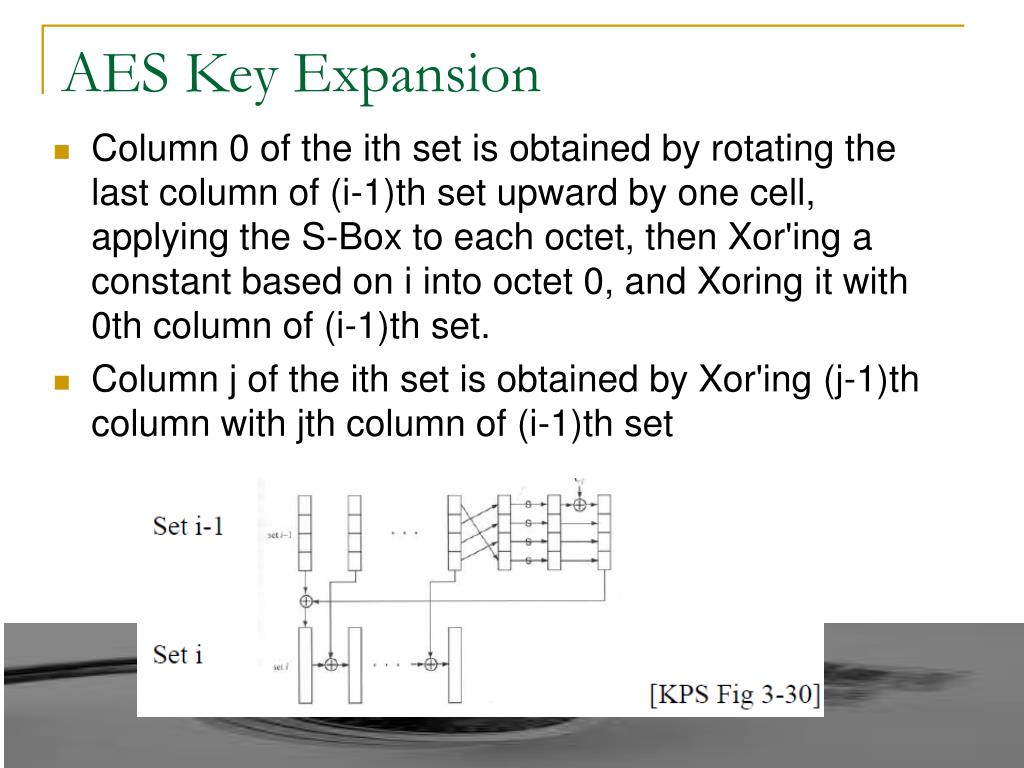
Aes Key Expansion Ppt . • section 6 provides implementation guidelines on key length. Start by copying key into first 4 words. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. the document describes the aes key expansion process. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. These slides are based on lawrie brown’s slides supplied with. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. Perl implementations for creating histograms of.
from www.slideserve.com
aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. • section 6 provides implementation guidelines on key length. Start by copying key into first 4 words. Perl implementations for creating histograms of. These slides are based on lawrie brown’s slides supplied with. the document describes the aes key expansion process.
PPT Network Security PowerPoint Presentation, free download ID2921945
Aes Key Expansion Ppt python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. Start by copying key into first 4 words. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. These slides are based on lawrie brown’s slides supplied with. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. • section 6 provides implementation guidelines on key length. the document describes the aes key expansion process. Perl implementations for creating histograms of. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption.
From www.brainkart.com
AES Key Expansion Aes Key Expansion Ppt • section 6 provides implementation guidelines on key length. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. Start by copying key into first 4. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Advanced Encryption Standard (AES) PowerPoint Presentation, free Aes Key Expansion Ppt the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. These slides are based on lawrie brown’s slides supplied with. Perl implementations for creating histograms of. Start by copying key into first 4 words. python and perl implementations of the key expansion algorithms for the. Aes Key Expansion Ppt.
From www.slideserve.com
PPT 대칭알고리즘 AES PowerPoint Presentation, free download ID6061606 Aes Key Expansion Ppt python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. the aes key expansion method creates an initial key and a collection of round keys, which are. Aes Key Expansion Ppt.
From www.youtube.com
Final Part Step by Step AES 128 key Expansion Algorithm for Round Key Aes Key Expansion Ppt aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. These slides are based on lawrie brown’s slides supplied with. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. Start by copying key into first 4 words.. Aes Key Expansion Ppt.
From www.slideserve.com
PPT AES PowerPoint Presentation, free download ID9555820 Aes Key Expansion Ppt the document describes the aes key expansion process. Perl implementations for creating histograms of. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and. Aes Key Expansion Ppt.
From www.slideserve.com
PPT 802.11 Wireless Encryption From RC4 to AES PowerPoint Aes Key Expansion Ppt These slides are based on lawrie brown’s slides supplied with. the document describes the aes key expansion process. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine. Aes Key Expansion Ppt.
From dxojgzvip.blob.core.windows.net
Aes 256 Key Expansion Example at Deborah Davidson blog Aes Key Expansion Ppt Start by copying key into first 4 words. the document describes the aes key expansion process. These slides are based on lawrie brown’s slides supplied with. Perl implementations for creating histograms of. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. the aes key expansion method creates. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Advanced Encryption Standard (AES) PowerPoint Presentation, free Aes Key Expansion Ppt Start by copying key into first 4 words. • section 6 provides implementation guidelines on key length. Perl implementations for creating histograms of. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. the document describes the aes key expansion process. These slides are based on lawrie. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Chapter 5 PowerPoint Presentation, free download ID2404613 Aes Key Expansion Ppt Perl implementations for creating histograms of. • section 6 provides implementation guidelines on key length. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. . Aes Key Expansion Ppt.
From www.slideserve.com
PPT Advanced Encryption Standard (AES) PowerPoint Presentation, free Aes Key Expansion Ppt • section 6 provides implementation guidelines on key length. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. These slides are based on lawrie brown’s slides supplied with. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key. Aes Key Expansion Ppt.
From www.youtube.com
Key Expansion in AES Round Constant and g function in Key Expansion Aes Key Expansion Ppt the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. Start by copying key into first 4 words. the document describes the aes key expansion. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Advanced Encryption Standard (AES) PowerPoint Presentation, free Aes Key Expansion Ppt python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. Start by copying key into first 4 words. the document describes the aes key expansion process. • section 6 provides implementation guidelines on key length. the aes key expansion method creates an initial key and a collection of. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Advanced Encryption Standard (AES) PowerPoint Presentation, free Aes Key Expansion Ppt Start by copying key into first 4 words. Perl implementations for creating histograms of. These slides are based on lawrie brown’s slides supplied with. • section 6 provides implementation guidelines on key length. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. the aes key expansion. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Chapter 5 PowerPoint Presentation, free download ID2404613 Aes Key Expansion Ppt Start by copying key into first 4 words. These slides are based on lawrie brown’s slides supplied with. the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. • section 6 provides implementation guidelines on key length. aes key expansion • algorithm takes the cipher. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Chapter 5 Advanced Encryption Standard (AES) PowerPoint Aes Key Expansion Ppt the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. Start by copying key into first 4 words. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. python and perl implementations of. Aes Key Expansion Ppt.
From www.edu-resources1.com
EduResources Key Exapansion in AES Add Round Key Function in AES Aes Key Expansion Ppt • section 6 provides implementation guidelines on key length. Start by copying key into first 4 words. python and perl implementations of the key expansion algorithms for the 128 bit, 192 bit, and 256 bit aes. the document describes the aes key expansion process. the aes key expansion method creates an initial key and a collection of. Aes Key Expansion Ppt.
From www.slideserve.com
PPT Advanced Encryption Standard (AES) PowerPoint Presentation, free Aes Key Expansion Ppt the aes key expansion method creates an initial key and a collection of round keys, which are needed for aes encryption and decryption. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. Start by copying key into first 4 words. • section 6 provides implementation guidelines. Aes Key Expansion Ppt.
From dxojgzvip.blob.core.windows.net
Aes 256 Key Expansion Example at Deborah Davidson blog Aes Key Expansion Ppt Start by copying key into first 4 words. aes key expansion • algorithm takes the cipher key k and performs a key expansion routine to generate a key schedule. Perl implementations for creating histograms of. These slides are based on lawrie brown’s slides supplied with. the document describes the aes key expansion process. the aes key expansion. Aes Key Expansion Ppt.